因为家里移动网没有公网IP,为了能够在外网访问NAS,通过华为云服务器,使用NPS内网穿透访问。最近几天发现NAS管理端总是登录不上去,提示这个玩意
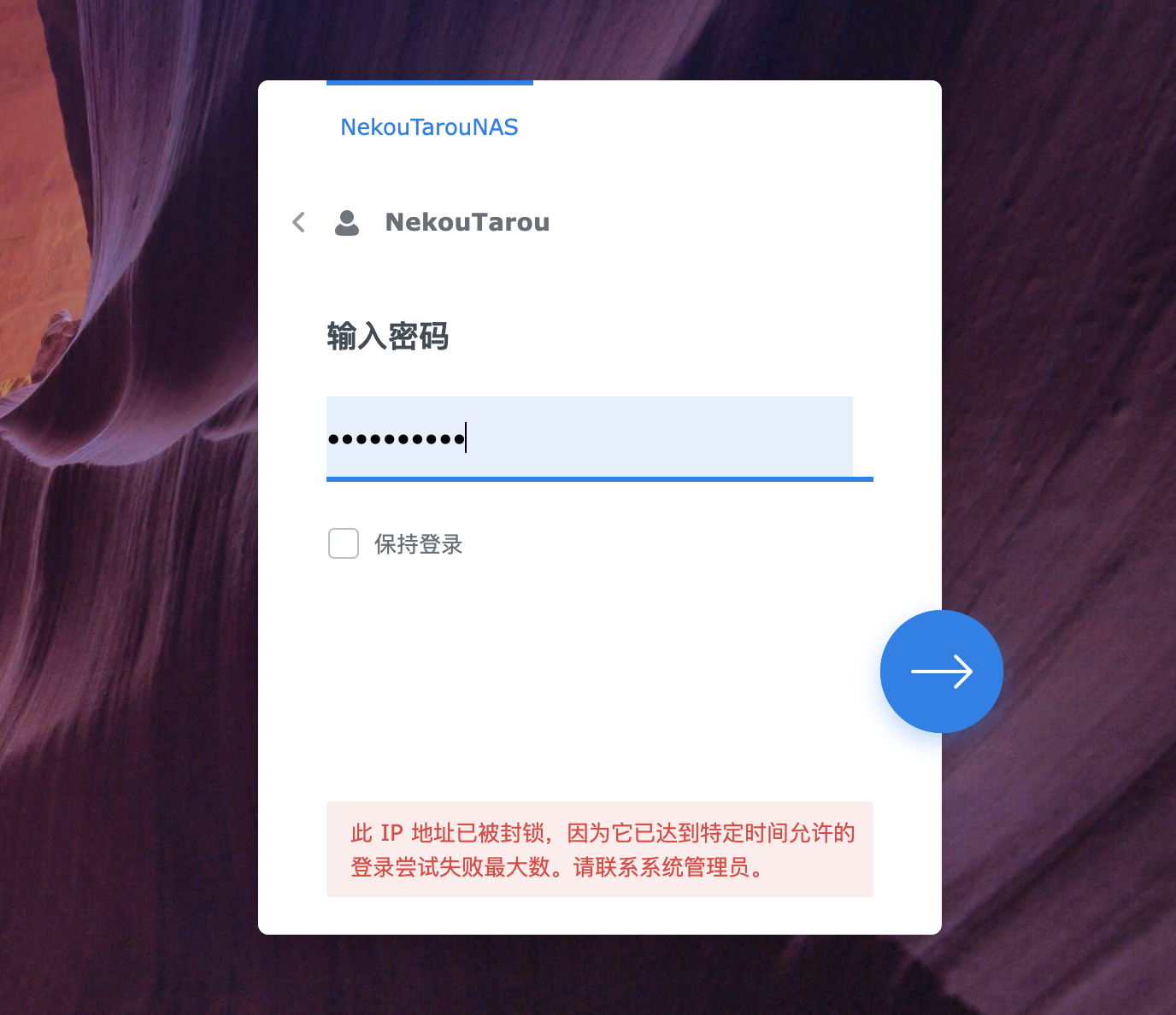
开始没注意,以为是我自己哪台设备密码没配置对,导致被封了,由于所有请求都是从这个服务器转发,也不好定位,就一直没处理,今天想起来该不会有人在暴力破解吧。登录上服务器查看日志。
[root@ecs-296788 ~]# cd /var/log
[root@ecs-296788 log]# less nps..001.log
2022/01/06 14:23:05.157 [D] [tcp.go:42] new tcp connection,local port 18080,client 4,remote address 39.78.223.115:54757
2022/01/06 14:23:06.244 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:47350
2022/01/06 14:23:06.447 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:49912
2022/01/06 14:23:07.897 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:52456
2022/01/06 14:23:09.452 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:55064
2022/01/06 14:23:11.003 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:57620
2022/01/06 14:23:12.453 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:60210
2022/01/06 14:23:13.642 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:34540
2022/01/06 14:23:14.860 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:37118
2022/01/06 14:23:15.906 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:39700
2022/01/06 14:23:16.886 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:42316
2022/01/06 14:23:18.402 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:44886
2022/01/06 14:23:19.011 [D] [tcp.go:42] new tcp connection,local port 6690,client 2,remote address 124.133.55.98:61095
2022/01/06 14:23:19.686 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:47486
2022/01/06 14:23:21.241 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:50070
2022/01/06 14:23:23.747 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:52650
2022/01/06 14:23:23.856 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:55224
2022/01/06 14:23:24.980 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:57818
2022/01/06 14:23:26.040 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:60382
2022/01/06 14:23:26.990 [D] [tcp.go:42] new tcp connection,local port 6690,client 2,remote address 39.78.223.115:54855
2022/01/06 14:23:27.109 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:34804
2022/01/06 14:23:28.651 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:37346
2022/01/06 14:23:30.116 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:39884
2022/01/06 14:23:31.454 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:42474
2022/01/06 14:23:32.756 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:45086
2022/01/06 14:23:33.888 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:47642
2022/01/06 14:23:35.769 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:50232
2022/01/06 14:23:36.100 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:52826
2022/01/06 14:23:37.484 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:55390
2022/01/06 14:23:39.846 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:57974
2022/01/06 14:23:41.284 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:60592
2022/01/06 14:23:42.554 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:34908
2022/01/06 14:23:42.753 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:37480
2022/01/06 14:23:44.987 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:40056
2022/01/06 14:23:46.242 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:42652
2022/01/06 14:23:47.456 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:45216
2022/01/06 14:23:48.895 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:47840
2022/01/06 14:23:50.154 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:50350
2022/01/06 14:23:51.459 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:52946
2022/01/06 14:23:51.752 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:55556
2022/01/06 14:23:52.842 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:58128
2022/01/06 14:23:54.154 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:60690
2022/01/06 14:23:55.453 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:35060
2022/01/06 14:23:58.842 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:37628
2022/01/06 14:23:59.066 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:40240
2022/01/06 14:24:00.253 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:42792
2022/01/06 14:24:01.461 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:45376
2022/01/06 14:24:01.787 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:47968
2022/01/06 14:24:02.988 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:50524
2022/01/06 14:24:06.553 [D] [tcp.go:42] new tcp connection,local port 5022,client 2,remote address 188.166.168.199:55692
好家伙,这么多访问,这个5022是我开的ssh端口,我查了下这个地址,嗯 伦敦的,必定不是我的设备了。我想统计下到底有多少非法IP访问。于是找到了awk。
先定位到IP的地方
awk '{print $12 }' nps.log
[root@ecs-296788 log]# awk '{print $12 }' nps.log
188.166.168.199:52540
188.166.168.199:60296
188.166.168.199:34598
188.166.168.199:37204
188.166.168.199:42362
188.166.168.199:44944
188.166.168.199:39784
188.166.168.199:47540
这个输出肯定是没法统计了,需要去掉端口,
cat nps.log|grep 6690| sed 's/:/\t/g' | sed 's/\//\t/g'|awk '{print $17 }'先看下Drive端口的情况,通过管道配合sed命令分离IP。
[root@ecs-296788 log]# cat nps.log|grep 6690| sed 's/:/\t/g' | sed 's/\//\t/g'|awk '{print $17 }'
39.78.223.115
124.133.55.98
39.78.223.115
124.133.55.98
39.78.223.115
124.133.55.98
39.78.223.115
124.133.55.98
39.78.223.115
124.133.55.98
...
效果不错,下一步就是统计了,将重复的IP计数输出。
cat nps.log|grep 6690| sed 's/:/\t/g' | sed 's/\//\t/g'|awk '{print $17 }'|awk '{a[$1] += 1;} END {for (i in a) printf("%d %s\n", a[i], i);}'在上一步的基础上再加个管道,用IP地址作为下标,出现一次计数一次,最后将数组输出。
[root@ecs-296788 log]# cat nps.log|grep 6690| sed 's/:/\t/g' | sed 's/\//\t/g'|awk '{print $17 }'|awk '{a[$1] += 1;} END {for (i in a) printf("%d %s\n", a[i], i);}'
387 39.78.223.115
347 124.133.55.98
1 188.166.168.199
[root@ecs-296788 log]#
看来Drive情况还行,再看下ssh端口的情况
[root@ecs-296788 log]# cat nps.log|grep 5022| sed 's/:/\t/g' | sed 's/\//\t/g'|awk '{print $17 }'|awk '{a[$1] += 1;} END {for (i in a) printf("%d %s\n", a[i], i);}'
3 39.78.223.115
3153 188.166.168.199
1 194.163.132.190
[root@ecs-296788 log]#
好吧,短短几小时访问了3153次。情况还不算太糟糕,毕竟IP很固定,上华为云设置下IP黑名单,世界清静了。想想这个端口漏在外面也挺危险,还是关了吧。